Base Roll: Users Guide: 
| ||
|---|---|---|
| Prev | Chapter 3. Defining and Modifying Networks and Network Interfaces | Next |
Rocks support of Virtual Machines requires the proper setup of networking bridges. Rocks supports multiple network adapters for Virtual Machines, In this section, we describe the various kinds of bridging scenarios for virtual machines and how to set them up. For these examples, the physical machine will be called vm-container-0-0,
When a VM is bridged to the physical device, it must be assigned in the same subnet as the physical device with a compatible IP address
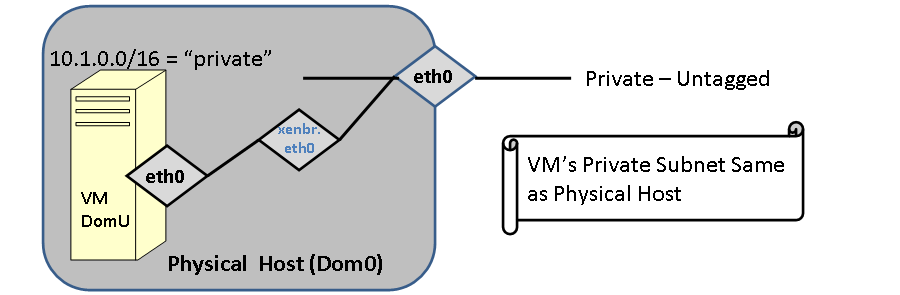
FIGURE: The Virtual machine is bridged to eth0. In this case eth0 of the VM is in the same subnet (with a compatible IP) address. The VM and the Container will be able to ping each other. This was the only configuration supported in Rocks 5.0
Use the following example shows this most basic of bridging scenarios. The guest (compute-0-0-1) and the container (vm-container-0-0) are in the same IP subnet ans will be able to ping each other.
[root@tranquil images]# rocks list host interface vm-container-0-0 compute-0-0-1 HOST SUBNET IFACE MAC IP NETMASK GATEWAY MODULE NAME VLANID compute-0-0-1: private eth0 00:16:3e:00:00:11 172.16.254.192 255.255.255.0 ------- xennet compute-0-0-1 ------ vm-container-0-0: private eth0 00:09:6b:89:39:68 172.16.254.238 255.255.255.0 ------- e1000 vm-container-0-0 ------ |
In this scenario, The guest (hosted-vm-0-0-2) and the host (vm-container-0-0) are not in the same logical network.
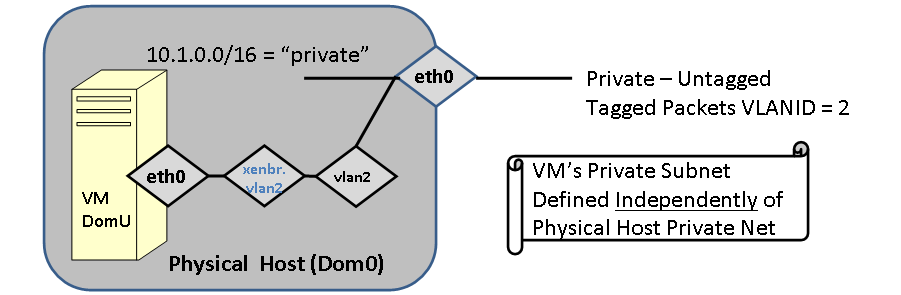
FIGURE: Guest VM is bridged through a logical VLAN devices.
[root@rocks ~]# rocks list host interface vm-container-0-0 hosted-vm-0-0-0 HOST SUBNET IFACE MAC IP NETMASK GATEWAY MODULE NAME VLANID hosted-vm-0-0-0: ------- eth0 00:16:3e:00:00:05 -------------- ---------- ------ ------ hosted-vm-0-0-0 2 vm-container-0-0: private eth0 00:0e:0c:5d:7e:5e 10.255.255.254 255.0.0.0 ------- e1000 vm-container-0-0 ------ vm-container-0-0: private vlan2 ----------------- -------------- --------- ------- ------ ---------------- 2 |
In the above configuration, Logical VLAN device vlan2 (with tag=2) will be on the physical network eth0 on vm-container-0-0. The hosted-vm-0-0 (a Rocks "appliance" that simply holds a generic VM guest) will have have its interface on VLANID=2. The physical machine must have a Logical vlan device with the same tag.
Below we, give a more complicated configuration and walk through exactly what is bridged where.
[root@rocks ~]# rocks list host interface vm-container-0-0 SUBNET IFACE MAC IP NETMASK GATEWAY MODULE NAME VLANID private eth0 00:0e:0c:5d:7e:5e 10.255.255.254 255.0.0.0 ------- e1000 vm-container-0-0 ------ net10 eth1 00:10:18:31:74:84 192.168.1.10 255.255.255.0 ------- tg3 vm-net10-0-0 ------ net10 vlan100 ----------------- -------------- ------------- ------- ------ ---------------- 100 private vlan2 ----------------- -------------- ------------- ------- ------ ---------------- 2 [root@rocks ~]# rocks list host interface hosted-vm-0-0-0 SUBNET IFACE MAC IP NETMASK GATEWAY MODULE NAME VLANID ------ eth0 00:16:3e:00:00:05 -- ------- ------- ------ hosted-vm-0-0-0 2 ------ eth1 00:16:3e:00:00:80 -- ------- ------- ------ --------------- 100 |
In the above scenario, if hosted-vm-0-0-0 (Xen guest, DomU) were to be booted on physical host vm-container-0-0 (Dom0), The packets from the guest on eth0 will be tagged with VLANID=2, and eth1 with VLANID=100. The host machine, must have Logical VLAN interfaces called "vlan*.". To make the proper bridge configuration, Rocks will match the VLANIDs of the guest interfaces to the VLANIDs on the host. On the host, logical interface vlan2 is labeled as being on the private network (eth0) and logical vlan100 is labeled as being on the net10 network (eth1). on
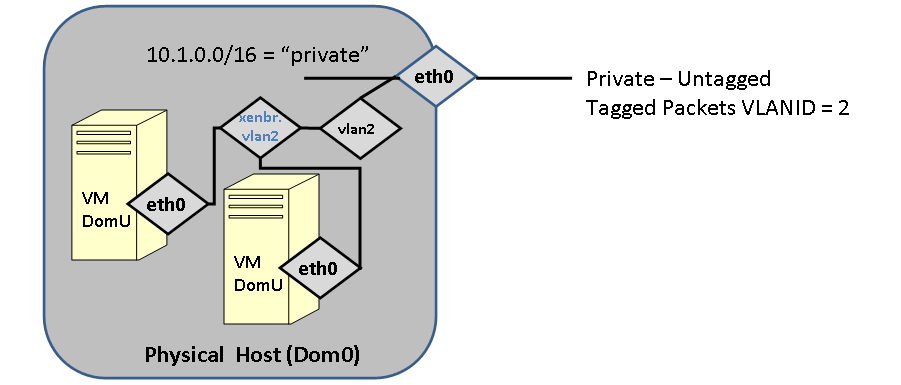
FIGURE: Multiple VMS communicating on a Logical VLAN interface.
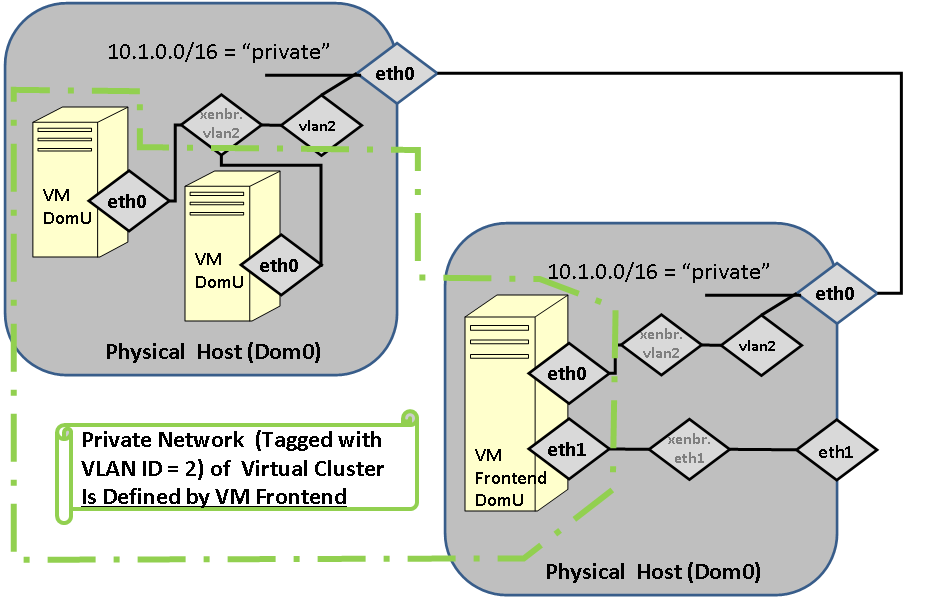
FIGURE: Fully Virtualized cluster, including a virtual frontend.